Introduction
A virtual private network (VPN) extends a private network across a public network so that you will be able to access your data remotely through the public network securely. You can also use a VPN to secure your internet activity by using the VPN server as a proxy server.
This article will show you how you can set up a VPN on a windows server machine step-by-step. Follow these easy instructions to set up your own VPN server.
This article will cover the setup of a VPN server which is commonly used for small environments. We recommend using Direct Access for enterprise purposes.
Prerequisites
You will need a Windows Server machine to use this article. We will be using a Windows Server 2016 as an example.
Step 1 Routing and Remote Access
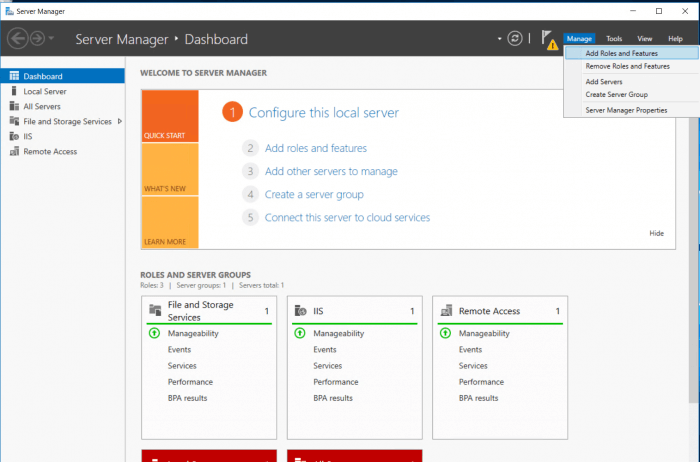
First, start with installing and setting up Routing and Remote Access. We will add the required features with the help of Server Manager. Open server manager and navigate to Manage>Add Roles and Features.
We want to add Remote access so proceed with checking ”Remote Access” in the Server Roles tab.

We will need the VPN role as well as Routing. We will be able to configure an internal NAT to assign internal IP addresses. Check ”DirectAccess and VPN(RAS)” and “Routing” in the Role services tab.

Check and proceed to the installation by confirming on the next screen.

We can now start with the setup of Routing and Remote access. Go to Tools> Routing and Remote Access. And Right-click on your server name. This will open a menu where you can select ”Configure and Enabling Routing…..”
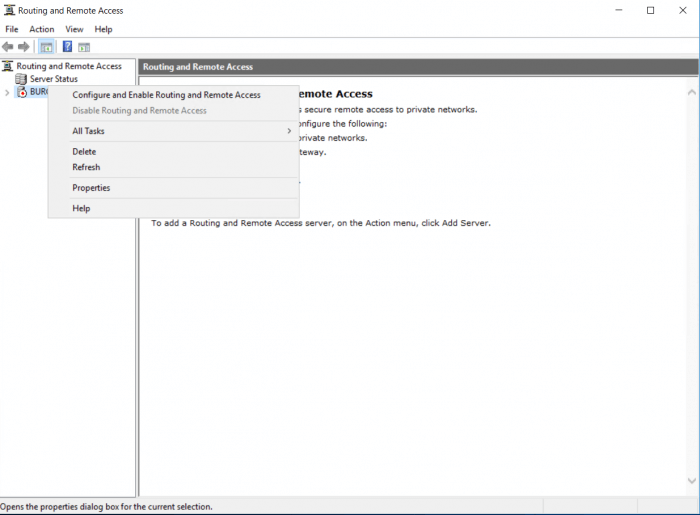
We will continue with Deploy VPN only this time to make this guide easy. Select “Deploy VPN only” in the new window

It’s important to select “Custom Configuration” in the next screen

We have now the option to select the services which we need. Select “VPN access” and ”NAT” and proceed.

Start the service and finish the setup. This can take a couple of minutes as the services are starting.

Step 2: Windows Firewall
It is possible that you will need to manually configure the Firewall. Please proceed if that’s the case
Open Windows Firewall with Advanced Security and go to Inbound rules > New Rule and select Predefined: Routing and Remote Access

Check the boxing according to the connection type you will use. We will check all three of the connection types in this case as we will have multiple clients which will need each of them. But you can limit it depending on your use to make it more secure.

Select ”Allow Connection” and Finish to complete the setup of the firewall.

Step 3: Configuring the IP range
We will now configure the IP range which the server will assign to the incoming VPN clients.
Open the Routing and Remote Access in Server Manager> Tools >Routing and Remote Access and right-click on your server name and go to Properties.

Go the IPv4 tab and select ”Static address pool” as the type of IPv4 address assignment.
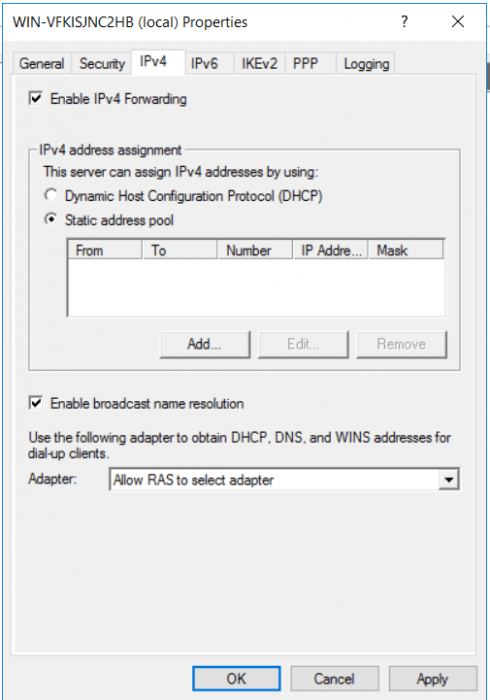
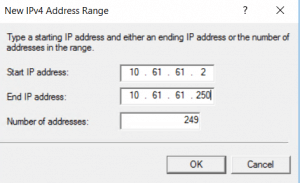
Add the range according to your needs. Each client will need his own IPv4 address. We will add a local range with 249 addresses. And click OK and OK to close the configuration
Step 4: Enable NAT
Configure the NAT to give your VPN clients internet access from the VPN. This is important if you want your users to be able to connect to the web. Right-click on NAT and add New Interface
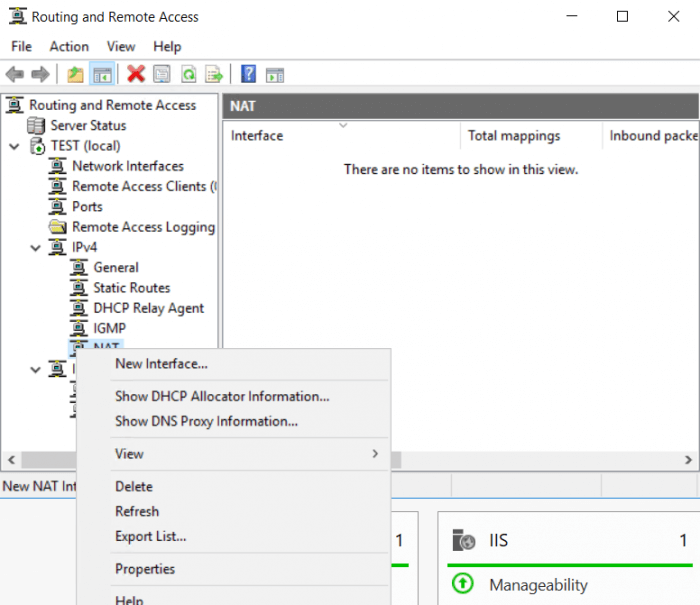
Select your main external interface. This is the interface that is connected to the outbound network.
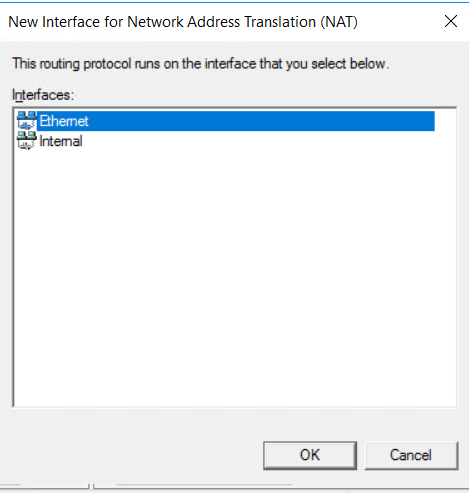
Check the following boxes to enable your clients to send and receive data using this interface.
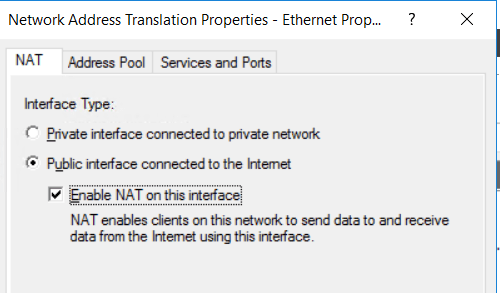
Go to the ”Service and Ports” Tab and select the following services. These services are required for a working NAT.

Beware each time you select a service a windows will pop-up. Fill in the address field ” 127.0.0.1” and continue. This is the IPv4 address for your local network.
You want to configure this was as this will enable your clients to use your VPN as the gateway.

Step 5: Configure access
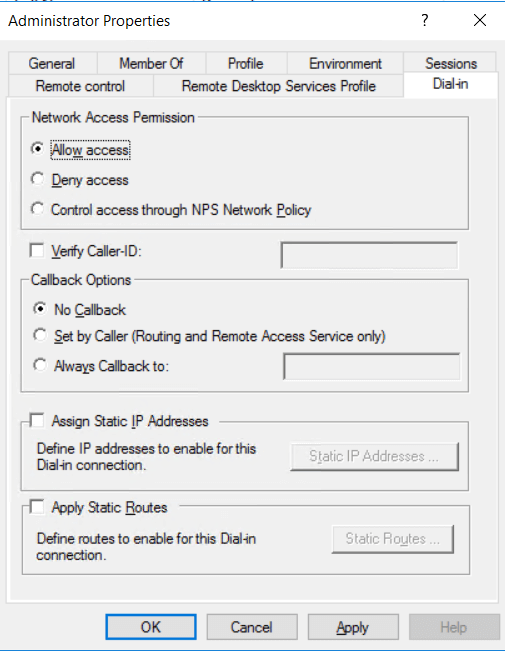
You will need to grant access for your local user(s) so that VPN users can use this account to authenticate.
Open your Computer management and go to Local Users and Groups. Right-click >”your user” and go to Properties.

Go to the tab Dial-in a select “Allow Access”
Step 6: Testing
You can check if the configuration works within the server and by testing it.
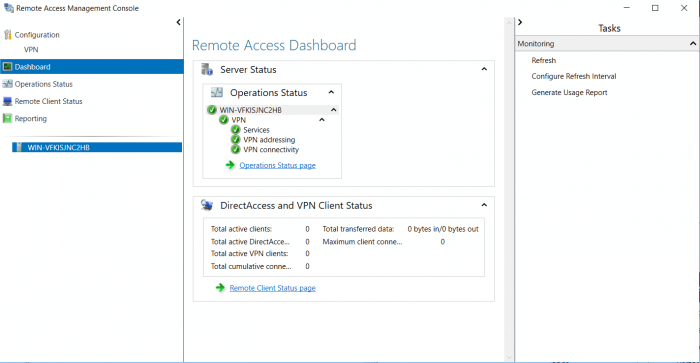
Open the Remote access Management console dashboard to see if all operation is up and running. You should see green icons next to the operations. Server Manager Tools &Remote access Management> Dashboard
Connect to the VPN with your local machine. In this case, we will connect using a Windows 10 machine.
Go to Settings>Network &Internet> VPN > Add a VPN connection And fill in the form

Save it then select the connection and click connect and done. You can continue by adding a VPN connection to your client-side machine.
Conclusion
After following all these steps, your Windows Server should now be set up for VPN connections. As mentioned in the introduction, a VPN is appropriate for smaller network deployments. Now you should have everything you need for your VPN use!



When connecting from the client computer (windows 10), which address must I put?
You need to enter the IP address of the server you want to connect to.
How many network adapters do you have and how do I use my public address
You can add up to 32 network adapters. If you configured the server as described in our article the traffic should leave the server on a Public IPv4 address.
Under Configure and Enable Routing and Remote Access, is there any specific reason why you selected "[x] Custom configuration" (and then checked "[x] VPN access" and "[x] NAT"), rather than "[x] Virtual private network (VPN) access and NAT" in the first place?
Thanks.
Great question, I don't think that would make any difference but I can't be sure without testing.
The reason why we using "[x] Custom configuration" instead of "[x] Virtual private network (VPN) access and NAT" is that "[x] Virtual private network (VPN) access and NAT" requires to have two or more network interfaces. It does not allow you to select this option if you have one network interface. See the warning here https://www.snel.com/wp-content/uploads/Screenshot-2019-06-25-at-14.45.39.png
This is a really great article. I successfully got it running on my first attempt, but ended up having to reformat the server and start over. The only difference is that I'm not using the machine as a Domain name controller. Could this have anything to do with why I can't connect from the outside?
No, you don't have to configure your server as a Domain Controller to have this working. There must be something else going on.
Thanks for the reply. I've got a dual port modem with the server hooked to the wan port but can't seem to hit via the external IP or the DNS address (mapped through no-IP). I can connect successfully from inside the network, and I can also ping my public IP and DNS address. Any other suggestions? Thank you for taking the time to read this and reply!
Is your server behind NAT? You need to forward port 3389 from your modem to your server to have this working from the outside!
Take a look at portforward dot com if you need help forwarding ports on your modem.
[edit] I’m sorry, I must be thinking RDP. 3389 (tcp) is for RDP and won’t help with VPN.
It’s advisable to run the VPN service on your router (if your router supports that). If your router doesn’t support that or you really want the VPN service on your Windows Server you may try the following:
– Enable VPN passthrough on your router (if your router has that option)
– Forward port 1723 tcp and Protocol 47 (GRE) for PPTP
– Forward port 500 and 4500 udp and Protocol 50 (ESP) for L2TP
Unfortunately not all of this is supported by every router.
We haven’t tried this and since this is heavily dependent on your router it’s worth giving it a shot but I can’t assure it works.
You are a genius, thanks so much. I’m going to try that when I get home.
Just another thing to let you know, this is one of the best guides I found for setting this up. There are tons of others, but they all missed the (super important) step of enabling the NAT for Internet sharing of connected clients. I pulled my hair out for hours before I found your guide. Thanks again!
Don't confuse protocols with ports.
Most common routers don't allow enabling or disabling protocols (usually all protocols are allowed)
Only reason I say this is that I've seen people forward port 47 and that is incorrect.
Yavuz Aydin, I assumed you wrote the above post on Introduction: Step-by-step guide VPN setup on Windows server.
Honestly, I had been browsing through google and most of them left out NAT setting. Your article really made my day, after struggling setting up for 3 weeks, now I am able to make it running. Thanks
Regards
Tun
Hello,
Thanks for the great info. Much Appreciated.
I got an issue. My client connect successfully to my remote server however I cannot access the internet. Am I missing something ?
I can RDP into my server in the cloud when VPN is connected.
Please assist
Could you provide more information about your client which your using and the current settings?
i'm having issue to setup once i reached until Go to Tools> Routing and Remote Access. And Right click on my server name the server by itself missing i only see server status on stuck over there
Are you not able to see "Configure and Enable Routing and Remote Access"?
yes i cant
I assume there you're missing some packages. My advice would be to re-apply step 1.
Okay i may not sure it seems need to click network policy access serves provide server roles admin provide local and remotes access
I have followed all of your steps. But my 'Remote Access Dashboard' does not show green. The 'active clients' information shows 'Unavailable'.
The only step that I could think of adding, and I've looked. Is opening a port in the ISPs firewall, which I did. For port 1723. But that port does not show open, when doing a port-scan. Yes I've added the rules in the Windows in-bound as it is stated above.
Anything else that I should be checking as to why it does not work?
Hey can anyone please advice is it secure or not because directly we are opening 1723 port on firewall to access RAS on server i am getting IPS and IDS alerts, even i checked event log of RAS hackers are trying to reach on server. Something like. How can we make it more secure ??
""CoId={NA}: The user vpn connected from 92.63.194.40 but failed an authentication attempt due to the following reason: The remote connection was denied because the user name and password combination you provided is not recognized, or the selected authentication protocol is not permitted on the remote access server.""
This article is deprecated, please use this article to set up a VPN on Windows Server 2016
Is it safe to open Routing and Remote Access (PPTP) on public profile in windows firewall?
I'm just going to say that I love you
Hi, Thank you for the nice article it was very helpful, I was able to connect to pptp vpn but can't access the shared drives from server, any idea what went wrong?
That's strange how are you trying to access the shared drive?